Relevant Products: Signature Manager Exchange Edition | Signature Manager Outlook Edition
WARNING! The following product was discontinued on 1st April 2021 and is no longer available for purchase or support:
- Mail Disclaimers
For more information, please see the Discontinued Questions and Answers page.
WARNING! The following products were discontinued on 30 September 2022:
- Exclaimer Signature Manager Outlook Edition
- Exclaimer Signature Manager Exchange Edition
The end of Support for these products is 30th September 2024.
For more information, please see the Discontinued Questions and Answers page.
You wish to manually apply the Application Impersonation permissions to your Admin account. Whether this is for the Signature Manager Outlook Edition Admin or your Local account to run the Sent Items Update or even the Exchange Mailbox Access account in Mail Archiver, this can be achieved by following the steps below.
Description
Due to the end of life of some Exchange systems, this is now only supported from Exchange Server 2010 Service Pack three and above.
Microsoft® Exchange 2010, Microsoft® Exchange 2013, Microsoft® Exchange 2016 and Microsoft® Windows® Small Business Server 2011
- Click Start > All Programs > Microsoft Exchange Server 2010/2013 > Exchange Management Shell:
A black PowerShell window is displayed.
- Enter the following command and press [ENTER]:
Get-MailboxDatabase | Add-ADPermission -User -AccessRights ExtendedRight -ExtendedRights ms-Exch-Store-Admin
- replace with the user account you wish to use.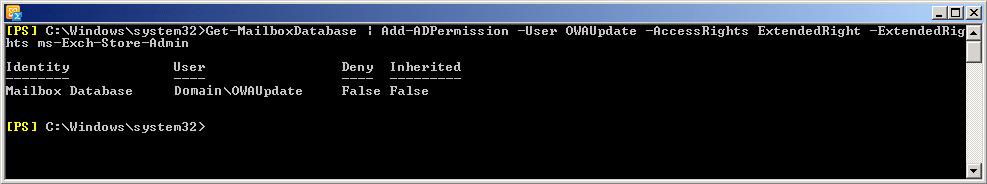
- Enter the following command and press [ENTER]:
$ExchangeServer = Get-ExchangeServer | where {$_.IsClientAccessServer -eq $true} | where {$_.IsValid -eq $true} | where {$_.IsExchange2007OrLater -eq $true} | where { $_.AdminDisplayVersion.Major -ge 14 } - Enter the following command and press [ENTER]:
$ExchangeServer | ForEach-Object { New-ManagementRoleAssignment -Role ApplicationImpersonation -User (Get-User -Identity "" | select-object).identity }
- replace with the user account you wish to use.
- Close the PowerShell window.
The user account you wish to use now has the required permission.